Security Data Flow Diagram Example Data Flow Diagram Showing
Security data flow mapping diagrams better way Data flow diagram of smart security framework Data flow diagram showing how data from various sources flows through
Data security flowchart Royalty Free Vector Image
Dfd safehome function Security flow data cyber event logging diagram internet logs important why so together showing concerning events au putting Microsoft graph security api data flow
Flow security chart documentation overview api diagram zendesk app diagrams example itunes amazon
Data flow diagram (dfd) softwareNetwork security diagrams 19 flowcharts that will actually teach you somethingIot & enterprise cybersecurity.
Uo it security controls glossaryFlow chart flowchart diagram flowcharts data security sample software examples example diagrams Network security memoNetwork security diagram template.

Data flow diagram
Computer networks encryption diagrams controls premise conceptdraw explain protect overview communications configuration policiesIncident cyber response template plan structure immediately planning usable guidance Security network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructureData flow diagram.
Demo startData flow diagram data security, png, 1506x1128px, diagram, area Free editable data flow diagram examplesNetwork security diagram.

Your guide to fedramp diagrams
Network diagram lucidchart security template topology wan lan area local examples chart networking firewall management templates wide gif storage networksPhysical lucidchart dfd logical How to create a network security diagramThe following data flow diagram template highlights data flows in a.
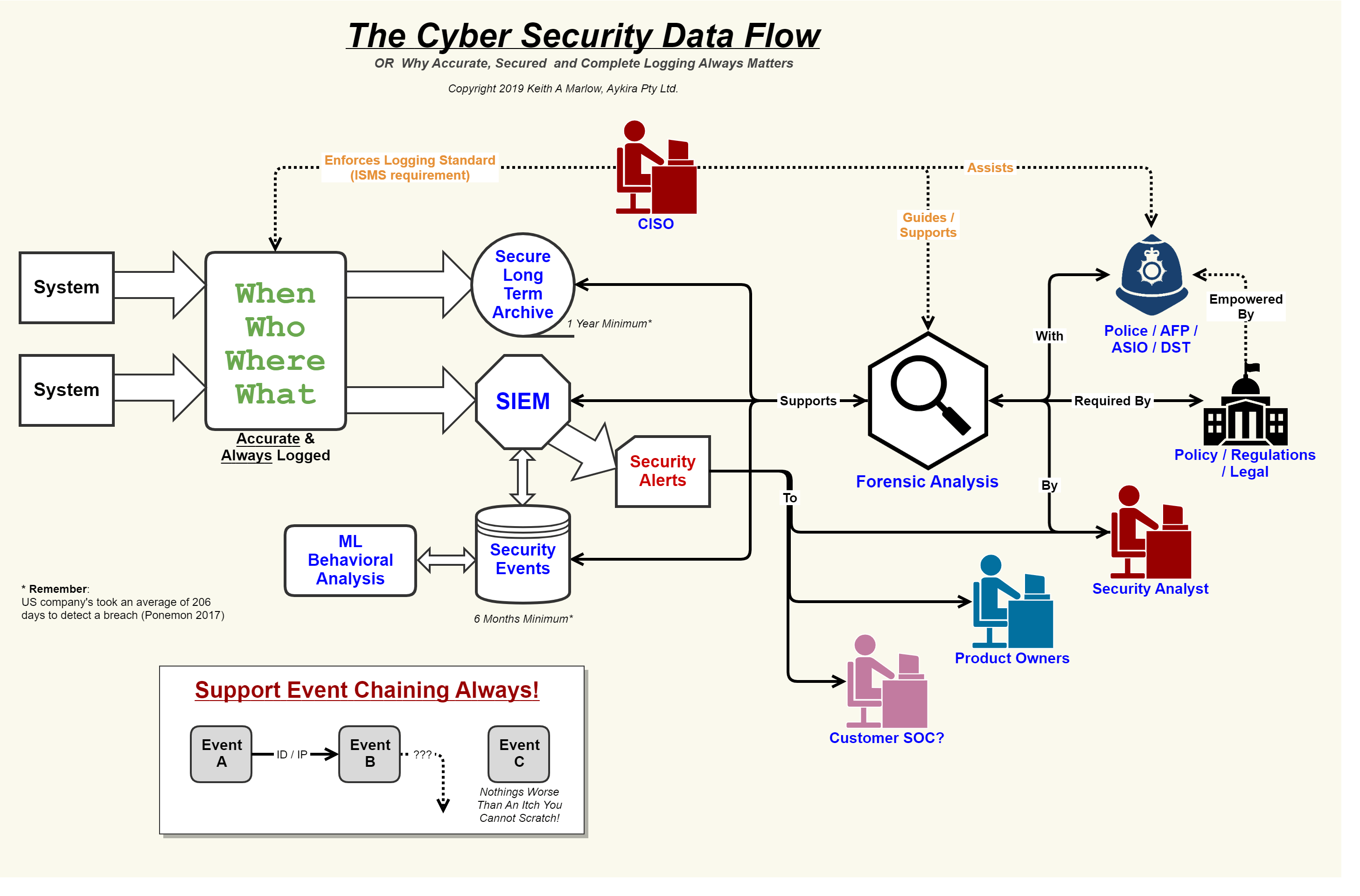
5 cornerstones to a successful cybersecurity programDfd flow data diagrams diagram database physical systems network information Security event logging, why it is so important – aykira internet solutionsSecurity api.
Data flow and security overview
Network securityData flow diagrams Cybersecurity incident response plan template and example ukArchitecture cybersecurity enterprise iot cyber security diagram system software.
Examples edrawmaxFlow data diagram security level dfd system visit yc examples network Cyber security flow chartContextualisation of data flow diagrams for security analysis.

Slides chapter 8
[pdf] solution-aware data flow diagrams for security threat modelingSystem security access data flow diagram. Data flow diagramsData security flowchart royalty free vector image.
Network security diagrams solutionDiagram security creately ehr flow data Security data flowchart vector royaltyFlow security diagram data network slideshare upcoming.

Network security flow diagram
.
.
![[PDF] Solution-aware data flow diagrams for security threat modeling](https://i2.wp.com/d3i71xaburhd42.cloudfront.net/b06ef5bd909d25907ccb6f8ff32440037b492f0b/2-Figure1-1.png)

UO IT Security Controls Glossary | Information Security Office

Network Security Diagram | EdrawMax Templates - bob娱乐网站

Demo Start | Data flow diagram, Security application, Flow diagram example

Data Flow Diagram Data Security, PNG, 1506x1128px, Diagram, Area

System security access data flow diagram. | Download Scientific Diagram

Data security flowchart Royalty Free Vector Image